Инсталиране на MySQL, Apache и PHPMyAdmin на Ubuntu Server
До тук имаме: - Инсталиран Ubuntu Server 22.04. - Базисно настроен Ubuntu Server 22.04, - Инсталиран и конфигуриран DNS сървис (BIND 9), - Име на хоста ns1.my.tlan.net, - Публично IP 185.163.245.186.
Инсталиране на MySQL (MariaDB)
sudo apt update -y sudo apt install mariadb-server -y [sudo] password for cccp: MyPa$$ sudo mysql_secure_installation NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY! In order to log into MariaDB to secure it, we'll need the current password for the root user. If you've just installed MariaDB, and haven't set the root password yet, you should just press enter here. Enter current password for root (enter for none): Enter OK, successfully used password, moving on... Setting the root password or using the unix_socket ensures that nobody can log into the MariaDB root user without the proper authorisation. You already have your root account protected, so you can safely answer 'n'. Switch to unix_socket authentication [Y/n] Enter Enabled successfully! Reloading privilege tables.. ... Success! You already have your root account protected, so you can safely answer 'n'. Change the root password? [Y/n] Enter New password: NewPa$$w0rd Re-enter new password: NewPa$$w0rd Password updated successfully! Reloading privilege tables.. ... Success! By default, a MariaDB installation has an anonymous user, allowing anyone to log into MariaDB without having to have a user account created for them. This is intended only for testing, and to make the installation go a bit smoother. You should remove them before moving into a production environment. Remove anonymous users? [Y/n] Enter ... Success! Normally, root should only be allowed to connect from 'localhost'. This ensures that someone cannot guess at the root password from the network. Disallow root login remotely? [Y/n] Enter ... Success! By default, MariaDB comes with a database named 'test' that anyone can access. This is also intended only for testing, and should be removed before moving into a production environment. Remove test database and access to it? [Y/n] Enter - Dropping test database... ... Success! - Removing privileges on test database... ... Success! Reloading the privilege tables will ensure that all changes made so far will take effect immediately. Reload privilege tables now? [Y/n] Enter ... Success! Cleaning up... All done! If you've completed all of the above steps, your MariaDB installation should now be secure. Thanks for using MariaDB! sudo mysql -u root -p [sudo] password for cccp: MyPa$$ Enter password: NewPa$$w0rd Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 41 Server version: 10.6.16-MariaDB-0ubuntu0.22.04.1 Ubuntu 22.04 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [(none)]> quit
Инсталиране на Apache
sudo apt update -y sudo apt install apache2 -y sudo apt install apache2-doc apache2-utils -y sudo systemctl status apache2.service ● apache2.service - The Apache HTTP Server Loaded: loaded (/lib/systemd/system/apache2.service; enabled; vendor preset: enabled) Active: active (running) since Tue 2024-04-23 07:04:23 UTC; 1min 18s ago Docs: https://httpd.apache.org/docs/2.4/ Process: 4882 ExecReload=/usr/sbin/apachectl graceful (code=exited, status=0/SUCCESS) Main PID: 4535 (apache2) Tasks: 55 (limit: 4558) Memory: 5.2M CPU: 59ms CGroup: /system.slice/apache2.service ├─4535 /usr/sbin/apache2 -k start ├─4890 /usr/sbin/apache2 -k start └─4891 /usr/sbin/apache2 -k start Apr 23 07:04:22 ns1.my.tlan.net systemd[1]: Starting The Apache HTTP Server... Apr 23 07:04:23 ns1.my.tlan.net apachectl[4534]: AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using ns1.my.tlan.net. Set the 'ServerName' directive globally to suppress this message Apr 23 07:04:23 ns1.my.tlan.net systemd[1]: Started The Apache HTTP Server. Apr 23 07:04:32 ns1.my.tlan.net systemd[1]: Reloading The Apache HTTP Server... Apr 23 07:04:32 ns1.my.tlan.net apachectl[4885]: AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using ns1.my.tlan.net. Set the 'ServerName' directive globally to suppress this message Apr 23 07:04:32 ns1.my.tlan.net systemd[1]: Reloaded The Apache HTTP Server. hostname -I 192.168.11.5
Проверяваме: http://my.tlan.net/
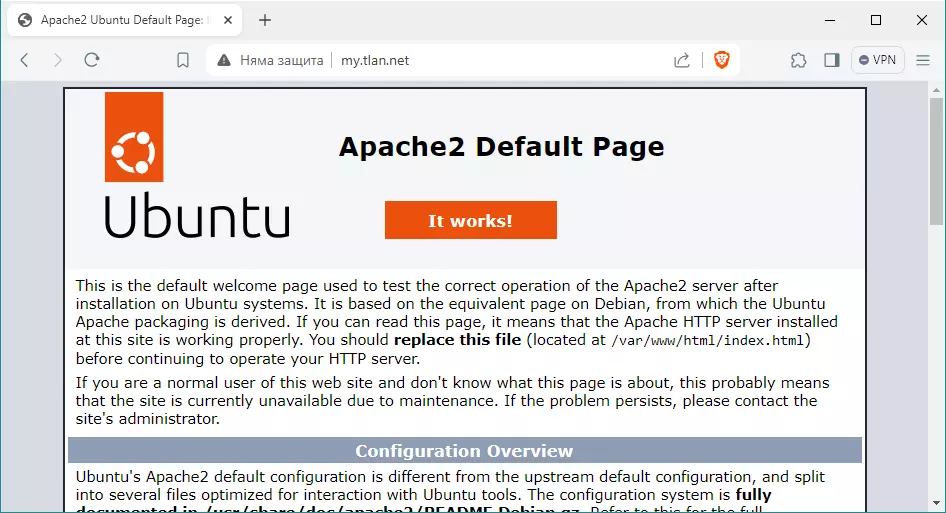
Работи.
sudo a2dissite 000-default.conf Site 000-default disabled. To activate the new configuration, you need to run: systemctl reload apache2 ls /etc/apache2/sites-enabled/
Нямаме инсталиран виртуален сайт.
sudo nano /etc/apache2/sites-available/my.tlan.net.conf <VirtualHost *:80> ServerName my.tlan.net ServerAlias mail.my.tlan.net ns1.my.tlan.net www.my.tlan.net DocumentRoot /var/www/my.tlan.net/ </VirtualHost> sudo mkdir -p /var/www/my.tlan.net sudo chown www-data:www-data /var/www/my.tlan.net sudo a2ensite my.tlan.net.conf Enabling site my.tlan.net. To activate the new configuration, you need to run: systemctl reload apache2 sudo service apache2 reload sudo service apache2 status
Да пробваме като напишем в браузъра http://my.tlan.net/.
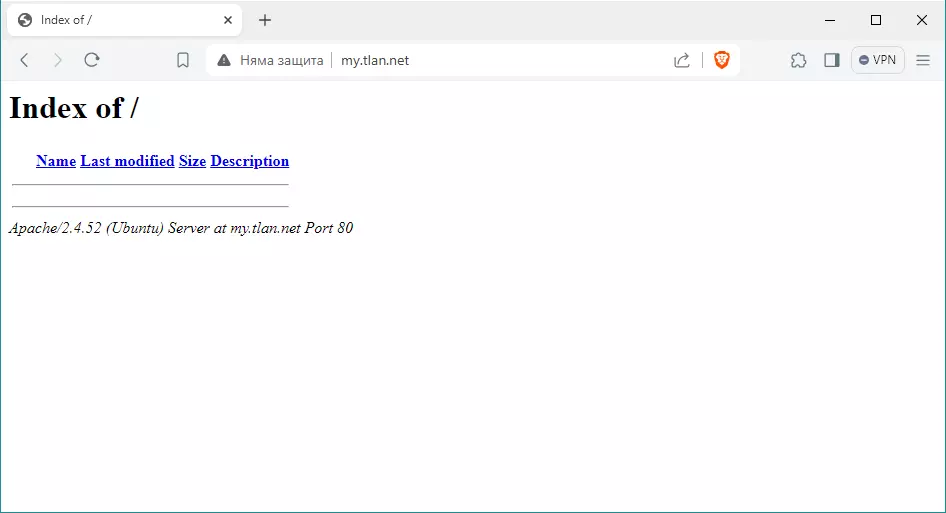
Рабитим със сайта. В случая показва празна папка, защото вътре няма никакви файлове. Да създадем един за тест.
sudo nano /var/www/my.tlan.net/test <!DOCTYPE html> <html> <body> <h1> My First Heading </h1> <p> My first paragraph. </p> </body> </html>
И наново тест чрез браузъра. http://my.tlan.net/test
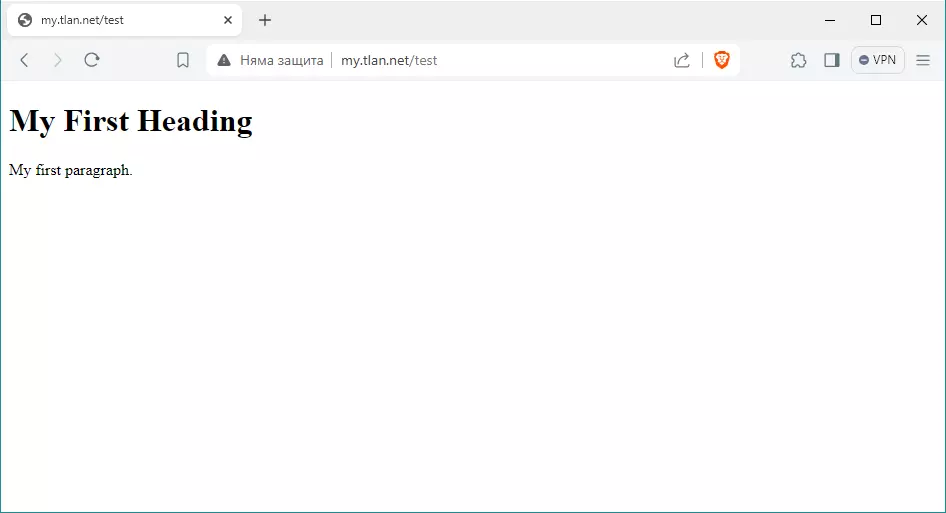
Супер, до тук всичко е наред. Отново повтарям, аналогични са действията и за виртуалния сайт my.tachko.com, който за сега няма да го разглеждаме. По-надолу ще покажа командите в сгъстен ред, без пояснения. Сега да накараме виртуалния хост да работи с https протокола.
sudo nano /etc/apache2/sites-available/my.tlan.net-ssl.conf <VirtualHost *:443> ServerName my.tlan.net ServerAlias mail.my.tlan.net ns1.my.tlan.net www.my.tlan.net DocumentRoot /var/www/my.tlan.net/ SSLEngine on SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key </VirtualHost>
Ползваме сертификатите получени по време на инсталацията (ssl-cert-snakeoil.pem и ssl-cert-snakeoil.key). Активираме виртуалния сайт отговарящ за HTTPS заявките.
sudo a2ensite my.tlan.net-ssl.conf Enabling site my.tlan.net-ssl. To activate the new configuration, you need to run: systemctl reload apache2
За да се работи със сертификати е необходимо и зареждане на модула ssl за Apache.
sudo a2enmod ssl
Рестартираме Apache за да влязат промените в сила.
sudo service apache2 restart
Тестваме като пишем в браузъра https://my.tlan.net/test
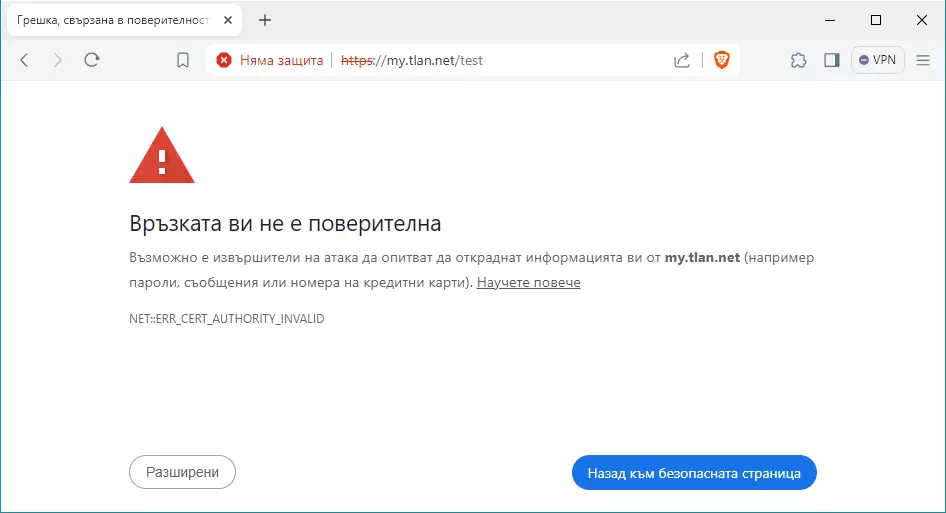
До тук всичко работи нормално. Проблема е, че сертификата не е публично удостоверен, но преди да продължим с темата да повторим операциите за виртуалния сайт my.tachko.com.
sudo nano /etc/apache2/sites-available/my.tachko.com.conf <VirtualHost *:80> ServerName my.tachko.com ServerAlias mail.my.tachko.com ns1.my.tachko.com www.my.tachko.com DocumentRoot /var/www/my.tachko.com/ </VirtualHost> sudo mkdir -p /var/www/my.tachko.com sudo chown www-data:www-data /var/www/my.tachko.com sudo a2ensite my.tachko.com.conf sudo nano /etc/apache2/sites-available/my.tachko.com-ssl.conf <VirtualHost *:443> ServerName my.tachko.com ServerAlias mail.my.tachko.com ns1.my.tachko.com www.my.tachko.com DocumentRoot /var/www/my.tachko.com/ SSLEngine on SSLCertificateFile /etc/ssl/certs/ssl-cert-snakeoil.pem SSLCertificateKeyFile /etc/ssl/private/ssl-cert-snakeoil.key </VirtualHost> sudo a2ensite my.tachko.com-ssl.conf sudo service apache2 reload
Готови сме и с my.tachko.com. Работи с протоколи http и https.
SSL от Let’s Encryp
Проблема обаче с публичните сертификати си остава. За целта ще ползваме услугата на https://letsencrypt.org/, наречена certboot. Първо да я инсталираме.
sudo apt install certbot python3-certbot-apache -y
Освен certboot инсталирахме и python3-certbot-apache. Тъй като работим с Apache за да интегрираме публичните сертификати е необходим плъгина за Apace на certboot. За начало да тестваме дали можем да генерираме сертификат за my.tlan.net, mail.my.tlan.net, ns1.my.tlan.net, www.my.tlan.net, my.tachko.com, mail.my.tachko.com, ns1.my.tachko.com, www.my.tachko.com
sudo certbot certonly --webroot --dry-run -w /var/www/my.tlan.net -d my.tlan.net -d mail.my.tlan.net -d ns1.my.tlan.net -d www.my.tlan.net -w /var/www/my.tachko.com -d my.tachko.com -d mail.my.tachko.com -d ns1.my.tachko.com -d www.my.tachko.com Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): tachko@my.tlan.net - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Account registered. Simulating a certificate request for my.tlan.net and 7 more domains The dry run was successful.
Теста мина без грешки Сега да създадем и интегрираме публичните сертификати.
sudo certbot --apache --agree-tos --redirect --hsts --staple-ocsp --email tachko@my.tlan.net -d my.tlan.net -d mail.my.tlan.net -d ns1.my.tlan.net -d www.my.tlan.net -d my.tachko.com -d mail.my.tachko.com -d ns1.my.tachko.com -d www.my.tachko.com Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Account registered. Requesting a certificate for my.tlan.net and 7 more domains Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/my.tlan.net/fullchain.pem Key is saved at: /etc/letsencrypt/live/my.tlan.net/privkey.pem This certificate expires on 2024-07-20. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. Deploying certificate Successfully deployed certificate for my.tlan.net to /etc/apache2/sites-enabled/my.tlan.net-ssl.conf Successfully deployed certificate for mail.my.tlan.net to /etc/apache2/sites-enabled/my.tlan.net-ssl.conf Successfully deployed certificate for ns1.my.tlan.net to /etc/apache2/sites-enabled/my.tlan.net-ssl.conf Successfully deployed certificate for www.my.tlan.net to /etc/apache2/sites-enabled/my.tlan.net-ssl.conf Successfully deployed certificate for my.tachko.com to /etc/apache2/sites-enabled/my.tachko.com-ssl.conf Successfully deployed certificate for mail.my.tachko.com to /etc/apache2/sites-enabled/my.tachko.com-ssl.conf Successfully deployed certificate for ns1.my.tachko.com to /etc/apache2/sites-enabled/my.tachko.com-ssl.conf Successfully deployed certificate for www.my.tachko.com to /etc/apache2/sites-enabled/my.tachko.com-ssl.conf Congratulations! You have successfully enabled HTTPS on https://my.tlan.net, https://mail.my.tlan.net, https://ns1.my.tlan.net, https://www.my.tlan.net, https://my.tachko.com, https://mail.my.tachko.com, https://ns1.my.tachko.com, and https://www.my.tachko.com We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Имаме създадени сертификати за https://my.tlan.net, https://mail.my.tlan.net, https://ns1.my.tlan.net, https://www.my.tlan.net, https://my.tachko.com, https://mail.my.tachko.com, https://ns1.my.tachko.com, and https://www.my.tachko.com. Да проверим чрез браузъра: https://my.tlan.net/test
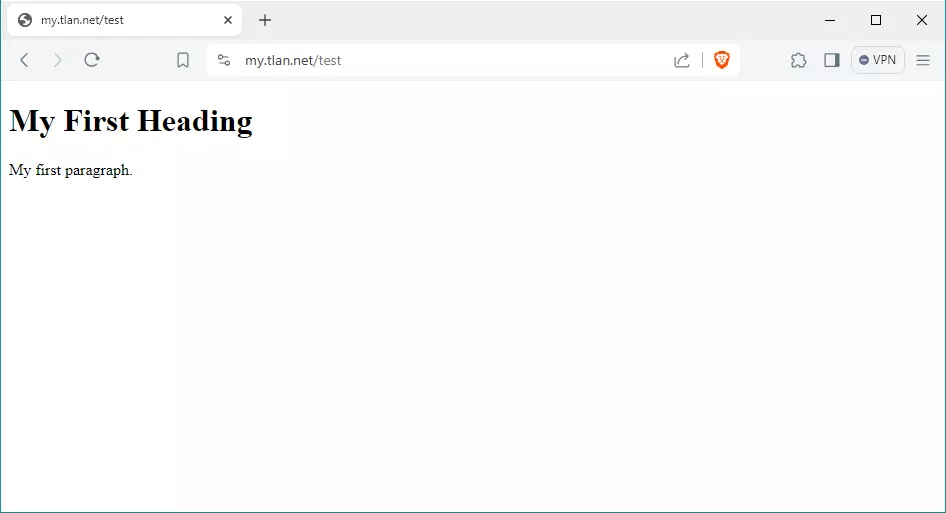
Всичко е наред имаме издаден сертификат и той е инсталиран където трябва. Пакетът certboot автоматично добавя времева задача която се изпълнява два пъти в деня на произволни часове. За да се подовява автоматино сертификата можем да ползвахме Cron или Systemd таймер. По-добрия вариант е втория. Таймера се определя във файла: /lib/systemd/system/certbot.timer За да разберем дали услугата е стартирана и кога ще е следващото събитеие изпълняваме:
sudo systemctl status certbot.timer
Независимо от всичко това има и Cron файл в: /etc/cron.d/certbot. Не се бъркайте, тази задача няма да направи нищо поради “-d /run/systemd/system”, което проверява дали systemd е инсталиран. А както знаем Debian използва systemd. До тук всичко е прекрасно, но автоматично ще се подновяват само файловете на сертификата. Проблем е, че компоненти като Apahche, PostFix и Dovecot няма да забележат промяната. За целта добавяме така наречения post-hook към certboot. Това ще рестартира всички гореспоменати процеси. За целата:
sudo nano /etc/letsencrypt/cli.ini # Най-отдолу добавяме: post-hook = systemctl restart apache2 # Ако имахме инсталирани още postfix и dovecot добавяме: post-hook = systemctl restart postfix dovecot apache2
Така вече всичко е наред. Сертификата автоматично ще се подновява на всеки 90 дена и след обновяването ще рестартира Apache, PostFix и Dovecot Между другото бях забравил. Да покажа какво и къде записа инсталацията на сертификата:
sudo nano /etc/apache2/sites-available/my.tlan.net.conf <VirtualHost *:80> ServerName my.tlan.net ServerAlias mail.my.tlan.net ns1.my.tlan.net www.my.tlan.net DocumentRoot /var/www/my.tlan.net/ RewriteEngine on RewriteCond %{SERVER_NAME} =my.tlan.net [OR] RewriteCond %{SERVER_NAME} =www.my.tlan.net [OR] RewriteCond %{SERVER_NAME} =mail.my.tlan.net [OR] RewriteCond %{SERVER_NAME} =ns1.my.tlan.net RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent] </VirtualHost> sudo nano /etc/apache2/sites-available/my.tlan.net-ssl.conf <VirtualHost *:443> ServerName my.tlan.net ServerAlias mail.my.tlan.net ns1.my.tlan.net www.my.tlan.net DocumentRoot /var/www/my.tlan.net/ SSLEngine on Include /etc/letsencrypt/options-ssl-apache.conf SSLCertificateFile /etc/letsencrypt/live/my.tlan.net/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/my.tlan.net/privkey.pem Header always set Strict-Transport-Security "max-age=31536000" SSLUseStapling on </VirtualHost> <IfModule mod_ssl.c> SSLStaplingCache shmcb:/var/run/apache2/stapling_cache(128000) </IfModule>
Виждат се къде се намират файловете на сертификата, също се вижда, че ползваме сертификати на letsencrypt.
Инсталиране на PHPMyAdmin
Има няколко варианта за инсталиранее на PHPMyAdmin. Единия е от репозиторите, а другия като го изтеглим от сайта и го инсталираме на ръка. Предпочитам първия вариант. По-лесен и ясен е според мен.
sudo apt update -y sudo apt upgrade -y sudo apt install wget php php-cgi php-mysqli php-pear php-mbstring libapache2-mod-php php-common php-phpseclib php-mysql php-zip php-gd -y sudo apt install phpmyadmin -y Configuring phpmyadmin ---------------------- The phpmyadmin package must have a database installed and configured before it can be used. This can be optionally handled with dbconfig-common. If you are an advanced database administrator and know that you want to perform this configuration manually, or if your database has already been installed and configured, you should refuse this option. Details on what needs to be done should most likely be provided in /usr/share/doc/phpmyadmin. Otherwise, you should probably choose this option. Configure database for phpmyadmin with dbconfig-common? [yes/no] yes Please provide a password for phpmyadmin to register with the database server. If left blank, a random password will be generated. MySQL application password for phpmyadmin: NewPa$$w0rdPHPMyAdmin Password confirmation: NewPa$$w0rdPHPMyAdmin Determining localhost credentials from /etc/mysql/debian.cnf: succeeded. Please choose the web server that should be automatically configured to run phpMyAdmin. 1. apache2 2. lighttpd (Enter the items or ranges you want to select, separated by spaces.) Web server to reconfigure automatically: 1
И сега ако напишем в браузъра: https://my.tlan.net/phpmyadmin/
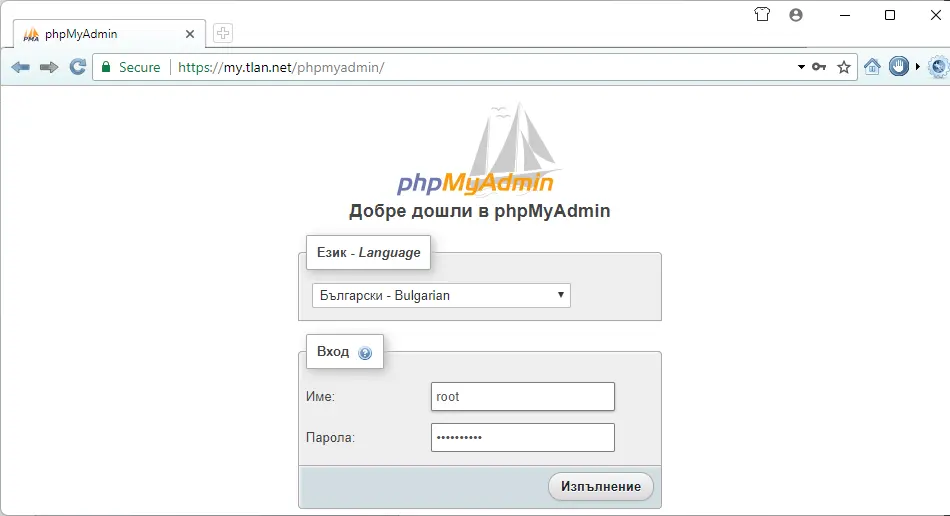
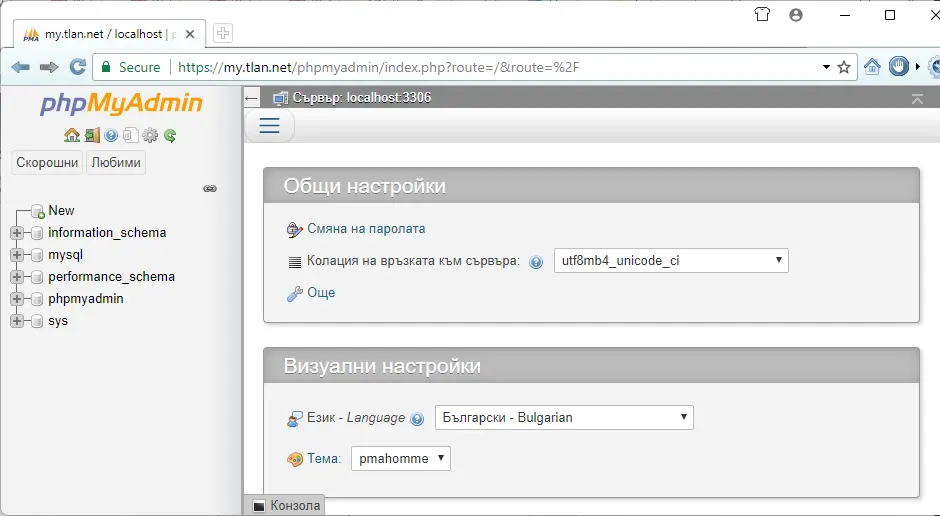
С това приключваме статията.